Secret military documents obtained by The Intercept offer rare documentary evidence of the process by which the Obama administration creates and acts on its kill list of terror suspects in Yemen and Somalia. The documents offer an unusual glimpse into the decision-making process behind the drone strikes and other operations of the largely covert war, outlining the selection and vetting of targets through the ranks of the military and the White House, culminating in the president’s approval of a 60-day window for lethal action.
The documents come from a Pentagon study, circulated in early 2013, evaluating the intelligence and surveillance technology behind the military’s Joint Special Operations Command (JSOC) killing campaign in Yemen and Somalia in 2011 and 2012.
The study, carried out by the Pentagon’s Intelligence, Surveillance, and Reconnaissance Task Force, illuminates and in some cases contradicts the administration’s public description of a campaign directed at high-level terrorists who pose an imminent threat to the United States. It admits frankly that capturing terrorists is a rare occurrence and hints at the use of so-called signature strikes against unknown individuals exhibiting suspicious behavior.
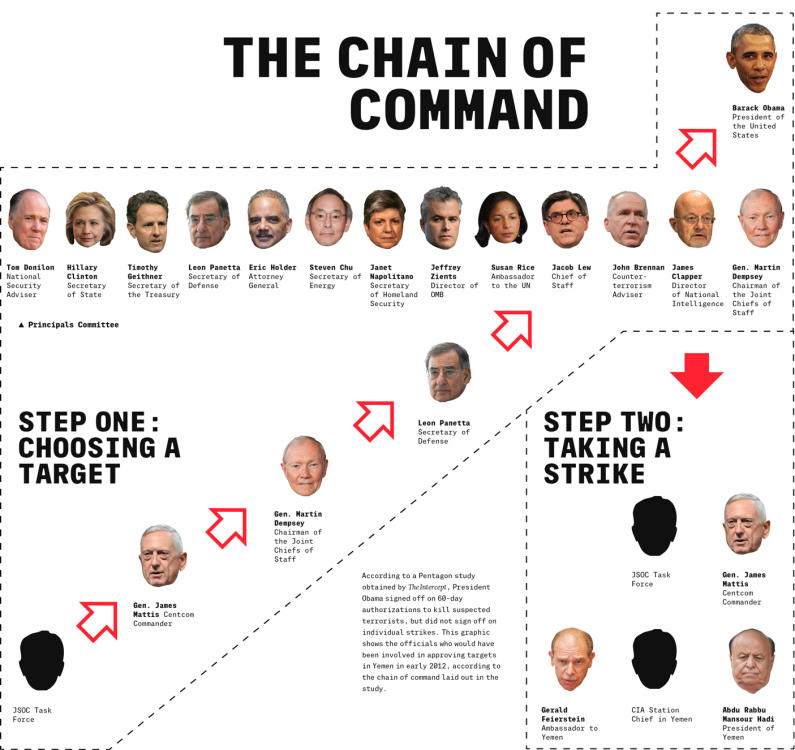
The Intercept obtained two versions of the study, a longer presentation dated February 2013, and an executive summary from May 2013, which includes a slide showing the chain of command leading to the approval of a lethal strike.
The Obama administration has been loath to declassify even the legal rationale for drone strikes — let alone detail the bureaucratic structure revealed in these documents. Both the CIA and JSOC conduct drone strikes in Yemen, and very little has been officially disclosed about either the military’s or the spy agency’s operations.
“The public has a right to know who’s making these decisions, who decides who is a legitimate target, and on what basis that decision is made,” said Jameel Jaffer, deputy legal director of the American Civil Liberties Union.
Both the Pentagon and the National Security Council declined to respond to detailed questions about the study and about the drone program more generally. The NSC would not say if the process for approving targets or strikes had changed since the study was produced.
Two Steps to a Kill
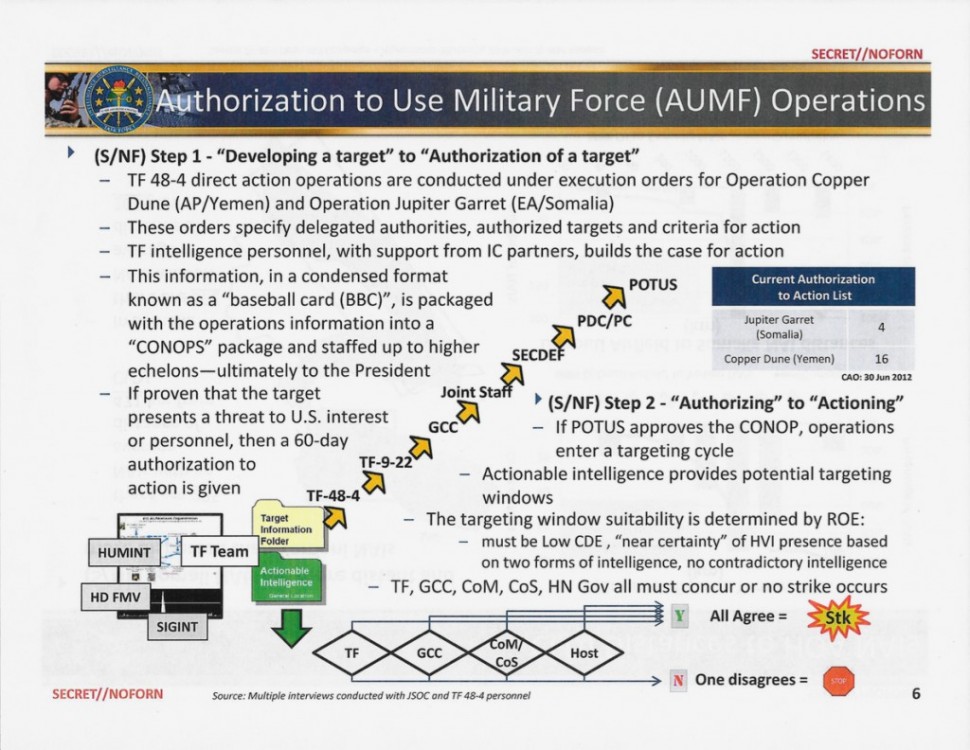
The May 2013 slide describes a two-part process of approval for an attack: step one, “‘Developing a target’ to ‘Authorization of a target,’” and step two, “‘Authorizing’ to ‘Actioning.’” According to the slide, intelligence personnel from JSOC’s Task Force 48-4, working alongside other intelligence agencies, would build the case for action against an individual, eventually generating a “baseball card” on the target, which was “staffed up to higher echelons — ultimately to the president.”
The intelligence package on the person being targeted passed from the JSOC task force tracking him to the command in charge of the region — Centcom for Yemen, and Africom for Somalia — and then to the Joint Chiefs of Staff, followed by the secretary of defense. It was then examined by a circle of top advisers known as the Principals Committee of the National Security Council, and their seconds in command, known collectively as the Deputies Committee.
The slide detailing the kill chain indicates that while Obama approved each target, he did not approve each individual strike, although news accounts have previously reported that the president personally “signs off” on strikes outside of Afghanistan or Pakistan. However, the slide does appear to be consistent with Obama’s comment in 2012 that “ultimately I’m responsible for the process.”
There have been various accounts of this drone bureaucracy, and almost all stress the role of Obama’s influential counterterrorism adviser John Brennan (who became director of the CIA in 2013) and of top administration lawyers in deciding who could be killed. Under Brennan, the nominations process was reportedly concentrated in the White House, replacing video conferences once run by the Joint Chiefs of Staff and elevating the role of the National Counterterrorism Center in organizing intelligence. Later in 2013, the White House reportedly tightened control over individual strikes in Yemen.
At the time of the study, with the president’s approval, JSOC had a 60-day window to hit a target. For the actual strike, the task force needed approval from the Geographic Combatant Command as well as the ambassador and CIA station chief in the country where the target was located. For a very important target, such as al Qaeda-linked preacher Anwar al Awlaki, who was a U.S. citizen, “it would take a high-level official to approve the strike,” said Lt. Col. Mark McCurley, a former drone pilot who worked on operations in Yemen and recently published a book about his experiences.
“And that includes a lot of lawyers and a lot of review at different levels to reach that decision. We have an extensive chain of command, humans along the whole link that monitor the entire process from start to finish on an airstrike.” The country’s government was also supposed to sign off. “One Disagrees = STOP,” the slide notes, with a tiny red stop sign.
In practice, the degree of cooperation with the host nation has varied. Somalia’s minister of national security, Abdirizak Omar Mohamed, told The Intercept that the United States alerted Somalia’s president and foreign minister of strikes “sometimes ahead of time, sometimes during the operation … normally we get advance notice.” He said he was unaware of an instance where Somali officials had objected to a strike, but added that if they did, he assumed the U.S. would respect Somalia’s sovereignty.
By 2011, when the study’s time frame began, Yemen’s president Ali Abdullah Saleh was in crisis. Facing domestic protests during the Arab Spring, he left the country in June 2011 after being injured in a bombing. Both the CIA and JSOC stepped up their drone campaigns, which enjoyed vocal support from Saleh’s eventual successor, Abdu Rabbu Mansour Hadi.
“It was almost never coordinated with Saleh. Once Hadi became president, March 2012, there was a big chance we’d be in the loop” before drone strikes were conducted, said a former senior Yemeni official who worked for both the Saleh and Hadi governments.
Today, with Yemen’s capital under the control of the Houthi rebel group and undergoing bombardment by Saudi Arabia, administration lawyers do not seem worried about asking permission to carry out drone strikes amid the fray.
“Now, I think they don’t even bother telling anyone. There is really no one in charge to tell,” said the former Yemeni official, who requested anonymity citing current unrest and the fact that he no longer works for the government.
Who Can Be Targeted
Both the Bush and Obama administrations have maintained that the 2001 Authorization for Use of Military Force, or AUMF, permits the pursuit of members of al Qaeda and its affiliates wherever they may be located.
The Pentagon study refers throughout to operations that fall under AUMF. But it also underlines how the targeted killing campaigns differ from traditional battlefields, noting that the region is located “Outside a Defined Theater of Active Armed Conflict,” which limits “allowable U.S. activities.”
Obama administration officials have said that in addition to being a member of al Qaeda or an associated force, targets must also pose a significant threat to the United States. In May 2013, facing increasing pressure to fully admit the existence of the drone war and especially to address allegations of civilian harm, the White House released policy guidelines for lethal counterterrorism operations that seemed to further restrict them. In a speech, Obama announced that action would be taken only against people who posed a “continuing, imminent threat to the American people,” and who could not be captured. A strike would only occur with “near certainty” that no civilians would be killed or injured.
Even with the new guidelines, legal observers, particularly human rights lawyers, have disputed the Obama administration’s position that the U.S., in strict legal terms, is in an armed conflict with al Qaeda in Yemen or Somalia — and therefore dispute what standards should apply to strikes. Others question the extent to which the hundreds of people killed in drone strikes in those countries meet the supposedly strict criteria.
“I think there can be questions raised about how stringently some of the requirements are being applied,” said Jennifer Daskal, an assistant professor of law at American University who worked for the Department of Justice from 2009 to 2011. “Near certainty of no civilian deaths, is that really imposed? What does it mean for capture not to be feasible? How hard do you have to try?”
It is not clear whether the study reflects the May policy guidance, since it does not give an extensive description of the criteria for approving a target, noting only that the target must be “a threat to U.S. interest or personnel.”
A spokesperson for the National Security Council would not explain why the standards in the study differed from the guidelines laid out in May 2013, but emphasized that “those guidelines remain in effect today.”
The two-month window for striking, says Hina Shamsi, director of the ACLU’s National Security Project, shows the administration’s broad interpretation of “a continuing, imminent threat.”
“If you have approval over a monthslong period, that sends the signal of a presumption that someone is always targetable, regardless of whether they are actually participating in hostilities,” said Shamsi.
The slide illustrating the chain of approval makes no mention of evaluating options for capture. It may be implied that those discussions are part of the target development process, but the omission reflects the brute facts beneath the Obama administration’s stated preference for capture: Detention of marked targets is incredibly rare.
A chart in the study shows that in 2011 and 2012, captures accounted for only 25 percent of operations carried out in the Horn of Africa — and all were apparently by foreign forces. In one of the few publicized captures of the Obama presidency, al Shabaab commander Ahmed Abdulkadir Warsame was picked up in April 2011 by U.S. forces in the Gulf of Aden and brought to Manhattan for trial, though he may not be reflected in the study’s figures because he was apprehended at sea.
The study does not contain an overall count of strikes or deaths, but it does note that “relatively few high-level terrorists meet criteria for targeting” and states that at the end of June 2012, there were 16 authorized targets in Yemen and only four in Somalia.
Despite the small number of people on the kill list, in 2011 and 2012 there were at least 54 U.S. drone strikes and other attacks reported in Yemen, killing a minimum of 293 people, including 55 civilians, according to figures compiled by the Bureau of Investigative Journalism. In Somalia, there were at least three attacks, resulting in the deaths of at minimum six people.
Some of those Yemen strikes were likely carried out by the CIA, which since mid-2011 has flown drones to Yemen from a base in Saudi Arabia and reportedly has its own kill list and rules for strikes. Yet it is also clear that the military sometimes harmed multiple other people in trying to kill one of those high-level targets. The study includes a description of the hunt for an alleged al Qaeda member referred to as “Objective Rhodes” or “Anjaf,” who is likely Fahd Saleh al-Anjaf al-Harithi, who was reported killed in July 2012, on the same day as Objective Rhodes. A failed strike on Harithi that April killed two “enemies.” News accounts at the time reported three “militants” had died.
The large number of reported strikes may also be a reflection of signature strikes in Yemen, where people can be targeted based on patterns of suspect behavior. In 2012, administration officials said that President Obama had approved strikes in Yemen on unknown people, calling them TADS, or “terror attack disruption strikes,” and claiming that they were more constrained than the CIA’s signature strikes in Pakistan.
The study refers to using drones and spy planes to “conduct TADS related network development,” presumably a reference to surveilling behavior patterns and relationships in order to carry out signature strikes. It is unclear what authorities govern such strikes, which undermine the administration’s insistence that the U.S. kills mainly “high-value” targets.
Near Certainty
According to the White House guidelines released in May 2013, the decision to take a strike should be based on thorough surveillance and only occur in the absence of civilians. A strike requires “near certainty that the terrorist target is present” and “near certainty that non-combatants will not be injured or killed.”
The study describes the rules for a strike slightly differently, stating that there must be a “low CDE [collateral damage environment]” — meaning a low estimate of how many innocent people might be harmed. It also states there must be “near certainty” that the target is present, “based on two forms of intelligence,” with “no contradictory intelligence.” In contrast to the White House statement, the “near certainty” standard is not applied to civilians.
The study cites the “need to avoiding [sic] collateral damage areas” as a reason for “unsuccessful” missions, but it does not give numbers of civilian casualties or examples of bad intelligence leading to a mistaken kill.
Yet the overall conclusion is that getting accurate positive identification is a “critical” issue for the drone program in the region, due to limitations in technology and the number of spy aircraft available. The military relies heavily on signals intelligence — drawn from electronic communications — and much of it comes from foreign governments, who may have their own agendas.
Identifying the correct target relates directly to the issue of civilian casualties: If you don’t have certainty about your target, it follows that you may well be killing innocent people. In Iraq and Afghanistan, “when collateral damage did occur, 70 percent of the time it was attributable to failed — that is, mistaken — identification,” according to a paper by Gregory McNeal, an expert on drones and security at Pepperdine School of Law.
Another factor is timing: If the 60-day authorization expired, analysts would have to start all over in building the intelligence case against the target, said a former senior special operations officer, who asked not to be identified because he was discussing classified materials. That could lead to pressure to take a shot while the window was open.
During the time of the study, there were multiple well-reported, high-profile incidents in which reported JSOC strikes killed the wrong people. Perhaps most famously, in October 2011, a 16-year-old U.S. citizen named Abdulrahman Awlaki, the son of Anwar al Awlaki, died in a JSOC strike while eating dinner with his cousins, two weeks after his father was killed by a CIA drone. In press accounts, one anonymous official called Abdulrahman’s death “an outrageous mistake,” while others said he was with people believed to be members of al Qaeda in the Arabian Peninsula. Publicly, the government has said only that he “was not specifically targeted.”
A September 2012 strike in Yemen, extensively investigated by Human Rights Watch and the Open Society Foundations, killed 12 civilians, including three children and a pregnant woman. No alleged militants died in the strike, and the Yemeni government paid restitution for it, but the United States never offered an explanation.
“The mothers and fathers and brothers and sisters of the people who were killed in these drones strikes want to know why,” said Amrit Singh, senior legal officer at the Open Society Justice Initiative. “We’re left with no explanation as to why they were targeted and in most cases no compensation, and the families are aware of no investigation.”
This spring, in a rare admission of a mistake in targeting, the White House announced that two hostages held by al Qaeda — an American and an Italian — had been killed in a CIA drone strike in Pakistan in January. In attempting to explain the tragedy, the White House spokesperson used the language of the standards that had failed to prevent it: The hostages had died despite “near certainty,” after “near continuous surveillance,” that they were not present.
3 WAYS TO SHOW YOUR SUPPORT
- Log in to post comments